The Traffic Light Protocol (TLP) v2 is a schema used to indicate with whom potentially sensitive information can be shared. Information sharing takes place from an information source towards one or more recipients.
TLP Labels
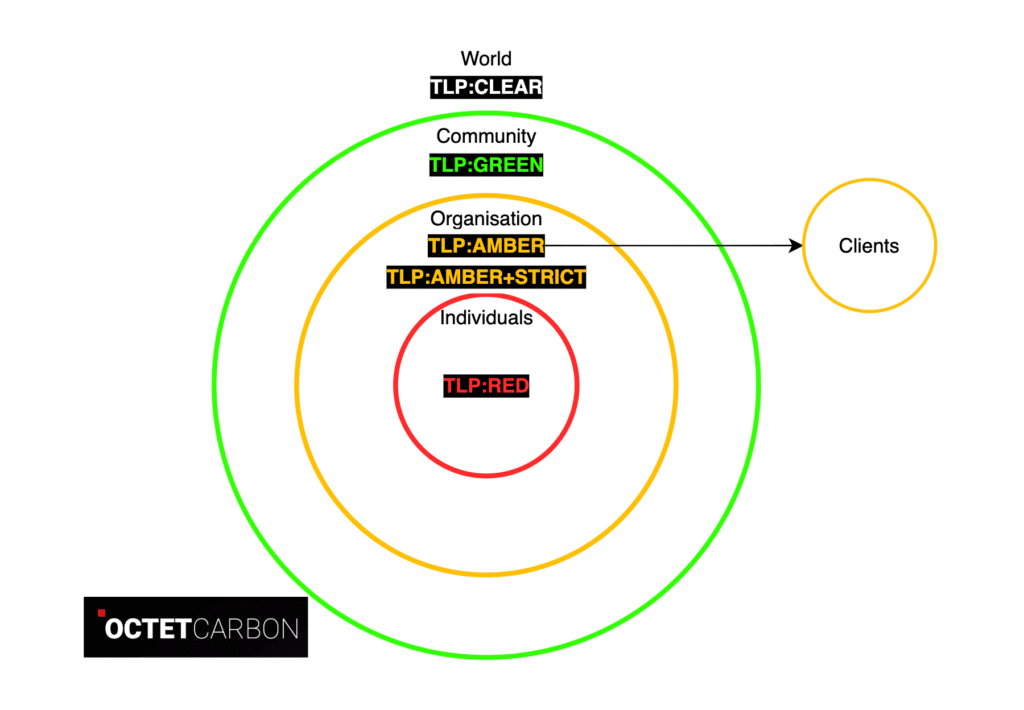
Under TLP, four labels are used to indicate the sharing boundaries to be applied by the recipients. These labels are:
- TLP:RED – For the eyes and ears of individual recipients only.
- TLP:AMBER – Limited disclosure; recipients can only share this information on a need-to-know basis within their organization and its clients.
- The source may use this label when the information to be shared requires support to be effectively acted upon, and disclosure carries risk to the privacy, reputation, or operations of the organisations involved.
- The recipients may share TLP:AMBER information with members of their own organisation and its clients on a need-to-know basis.
- The source may useTLP:AMBER+STRICT to restrict information sharing to the organisation only—excluding the organisation’s clients from this sharing.
- TLP:GREEN – Limited disclosure; recipients can share this information within their community.
- The source may use this label when the information to be shared is useful for increasing awareness within their wider community.
- The recipients may share TLP:GREEN information with peers and partner organisations within their community (e.g., cybersecurity/defence community), but not via public channels.
- TLP:CLEAR– No limit on disclosure; recipients can share this information freely with the public.
Note that TLP labels must remain in their original form, even when the content is translated into other languages. In other words, the content can be translated, but the labels themselves cannot. Moreover, TLP is not a formal classification schema, licensing term, or information handling/encryption rule.
Additionally, TLP sets rules between senders and recipients who wish to comply with the protocol while using the labels. These rules are:
- The source must ensure that recipients of TLP-labeled information understand the TLP sharing guidance and can follow it.
- The source may specify additional sharing restrictions, and recipients must adhere to those restrictions.
- Recipients must obtain explicit permission from the source if they need to share information beyond the boundaries specified in the TLP table.
TLP Usage
- In messaging (such as email or chat), the source must indicate the TLP label of the information, as well as any additional restrictions, directly prior to the information itself.
- In the case of email, the TLP label should appear in the subject line of the email and at the end of the text to which the TLP label applies.
- In documents, the source must indicate the TLP label of the information, as well as any additional restrictions, in the header and footer of each page. It is recommended to use 12-point type or greater for the TLP label and align it to the right.
- In automated information exchange, TLP usage is not formally defined and is left to the designers of such exchanges. However, it must remain consistent with the TLP standard.
At Octet Carbon, we promote trusted frameworks like TLP to enhance secure communication and risk management.
Additional Links
- TLP v2 (https://www.first.org/tlp/)
- TLP v1 (https://www.first.org/tlp/v1/) – Deprecated
Comment Policy
We welcome thoughtful discussion and questions. Comments are moderated and may be edited or removed if they contain spam, offensive language, or off-topic content. Thanks for keeping the conversation respectful!